TL;DR
- WordPress creates Author Archives pages for anyone who publishes content on a website sometimes keeping that page live even if that content is transferred to another user.
- By default WordPress uses the ‘username’ a user logins in with for the Author Archive page URL and offers no way of changing this.
- When Yoast is installed sitemaps are activated by default creating an Author Archive sitemap which contains all the Author URLs complete with usernames.
- Hackers can use this file to gain important usernames for a website, making hacking easier by only needing to guess passwords.
- This attack vector can be patched by turning off Author Archives in Yoast or if Author Archives are required by editing the URL of author archives in the WordPress code.
Update: Yoast was notified of my concerns earlier this week, has fully reviewed them, and responded. Essentially in their response they stated this wasn’t much of a concern to them though they had discussed it and offered tips. I’ve placed their entire response at the bottom of this article, you can get there by clicking here.
Yoast is a wildly popular WordPress plugin that helps websites become more SEO friendly. I use it on every single WordPress SEO project I work on and according to the WordPress repository there are 5 million other websites out there with it installed as well.
Recently I noticed a client’s website had failed login attempts from actual usernames while reviewing logs (I use Simple History). 2 of the usernames had never published anything on the website, all 3 had their “Public Display Name” set to something else. I checked the theme and there was nothing in the code revealing user names anywhere. One of those usernames was me, the others were the staff website admin and a locally based developer working on contract. I contacted them both to make sure they didn’t fail to login recently, knowing that I hadn’t had issues. No one had problems logging in recently. There are multiple ways for usernames to leak out of WordPress, the staff developer team informed me they had patched all known ways. There shouldn’t have been any way for these usernames to show to hackers and they shouldn’t be in the records as a failed login attempt. Even worse the ip addresses on the failed logins mapped to Poland, Ukraine, Russia, and South Korea. The client and none of their employees or contractors (or myself) had recently visited any of those places.
All websites can be hacked. To hack a website with a CMS like WordPress hackers tend to most frequently use what is known as a brute force attack. This is where they guess at the username and password of a website randomly using what they think are the most likely combinations first and then going on from there. Brute force attacks are only as effective as the information they have. For example, you might know someone who has had their Facebook account hacked. To do this hackers typically need to know the login email address (or guess it) and then only need to guess the password. In the early days it was easy to obtain Facebook login emails because they were displayed by default to friends of friends under the ‘about’ section of a user’s profile. All hackers had to do was get people to accept them as friends and then go and copy all the email addresses they could. This is why 2-Factor Authentication has seen a meteoric rise in many areas of the web and why Google’s recaptcha exists – to try and stop automated login attempts which are likely malicious in nature.
Unfortunately out of the box WordPress doesn’t have very many protections built in to login security and one of those flaws becomes like a lighthouse to hackers once Yoast is installed. To make sure I’m being clear here, Yoast doesn’t cause this attack vector, they just make it much easier for hackers to find and don’t offer many ways of stopping it.
When you install the Yoast SEO plugin on WordPress by default it keeps enabled what are called “Author Archives”. These archives are built into the core of WordPress to help users find content written by an author they like and can help search engines like Google find older content on a website. Yoast recommends that for single-author websites (like this one) that webmasters disable the archives, though they never really go into details as to why.
An SEO best practice is to install what are known as Sitemaps. These are XML files that help organize content on a website for a search engine to crawl and better understand. One of the best features with Yoast is that it includes these XML sitemaps turning them on by default and allows users to determine what content they want in sitemaps and what types of sitemaps to display. The moment you activate Yoast it automatically creates an Author Sitemap which links to these author archive pages – in some cases even if an author doesn’t have any currently published content on the website (old content set to draft or content assigned to someone else still places the URL in the sitemap). The URL structure for these archive pages is typically: website.com / author / [Username].
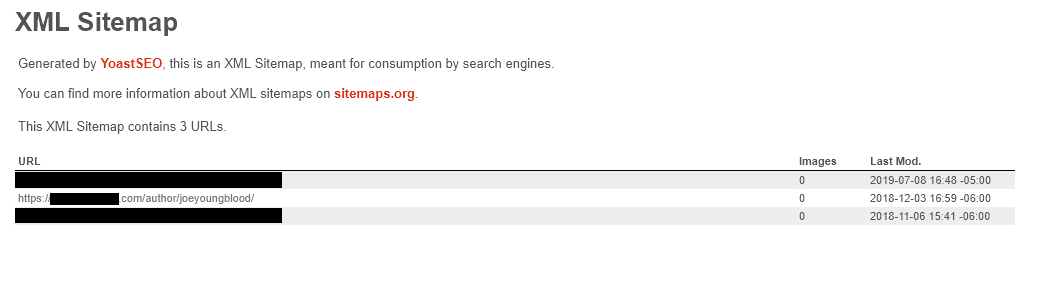
Unfortunately, if you leave the author archives enabled for any amount of time after installing Yoast, you have given hackers half of the information they need to go from a randomized automated hacking attempt to a more targeted attack on your website. (Depending on which WordPress theme you’re using the posts and pages may or may not already be giving that information to hackers. However, even if they are not, Yoast seems to do a good job of it.)
There also doesn’t appear to be any way to edit these URLs to use a different structure such as FirstName-LastName either directly in WordPress or in Yoast. That means the moment you create a piece of content as a user if Author Archives are turned on (default setting in WordPress and Yoast) and sitemaps are generated (default setting in Yoast), then hackers can simply scan a site for the author XML sitemap, download the links, and strip out everything before the username (and the trailing slash) to snag all of the important usernames on the website to better target their attacks. This makes finding usernames on a WordPress site relatively simple and low cost for potential attacks.
If a writer or website admin uses the same username across several websites this could make them an even larger target for an attack as it increases the likelihood of a successful attack and the likelihood of that user having advanced permissions on at least one website.
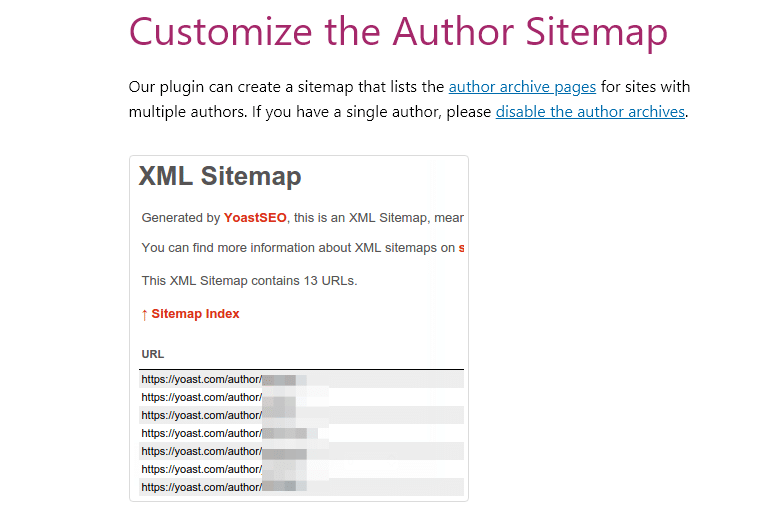
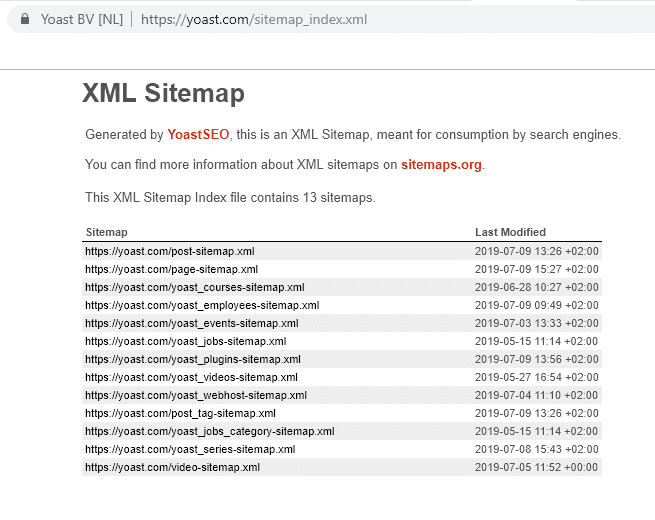
Worse even yet, Yoast may even know about this attack vector and may not be doing enough to educate users themselves on the inherent dangers. On their website under the article “Customize the Author Sitemap” Yoast blurs out the usernames in a screenshot of their Author Sitemap file URLs. In fact, Yoast actually has this feature turned off on their own website as you can see below.
What Yoast can do to make WordPress sites more secure
1. I don’t think Yoast should be forcing websites to all turn off author archives like some might suggest. While it’s not a feature everyone needs having it turned off when installing Yoast would cause problems with those websites that rely on it.
2. Do not turn on Author sitemaps by default. They should be a separate thing turned on only by a more savvy SEO who has either taken appropriate steps to safegaurd the usernames or is aware of the potential dangers.
3. Pages on their website about Author Archives should clarify the potential problems using Author based Archives might have.
4. The notices under “Archives” in their SEO plugin should alert of the dangers of the WordPress author archive URLs.
5. Yoast should offer a way to change Author Archive URLs inside of their plugin and make this a recommended step.
Here’s how to fix this attack vector in Yoast & WordPress
1. When you install Yoast (which I still recommend) toggle off the Author Archives immediately. If you do this Yoast will turn off the Author sitemap which means hackers won’t find the author sitemap and easily scrape usernames.
2. You can make doubly sure that username information doesn’t get found by checking the box next to “Do not allow search engines to show this author’s archives in search results.” in each important users settings page at the bottom under “Yoast Settings”.
3. You can try installing a plugin based solution that will allow you to customize the slug for author archives like this one. The Edit Author Slug plugin has been updated recently and appears to be updated regularly since 2013. This will allow you to make a different slug for the author archive and keep from displaying the username in the URL.
4. You can edit the code of your theme to not display usernames or have your theme developer write code to change the slug or URL for author archives to something else.
Security Note: This is known as “Security by Obscurity” and won’t make your website bulletproof and shouldn’t be considered a long-term security option. While it will lead to a decrease in brute force attack attempts, especially targeted ones, it doesn’t make the other attempts more difficult. There are other ways to help make your website secure such as limiting login attempts or changing the URL of the WordPress admin login page. I recommend consulting with your company’s I.T. / Security team on what is best for your website. This article was only intended to make users aware of an inherent security problem with WordPress and the popular Yoast plugin.
Yoast’s Response
Hi Joe,
Thank you for your patience and it’s awesome to hear you are an avid user of our plugin.
You raise some valid security concerns. We have discussed them internally as well. First of all, let’s make it clear that there is a distinction between usernames and authors. With that thought in mind, we’ll share our view on the matter:
- We only output authors in the XML sitemap, not all users.
- WordPress outputs author names all over the place; our XML sitemaps only make it fractionally easier for people to harvest. Many themes include the page author as a body class, for example. All of the JSON endpoints do by default, too. Trying to hide/remove those author names from everywhere is a mission.
- Most themes link to the author URL page in every post, for example, the link to your author page here.
- Rewriting the path of author archives is a breaking change.
- Lastly, we recommend not writing articles/posts with your admin account but creating a second user with only editor rights as the author to write your blog posts (see article: https://yoast.com/wordpress-security/#editoraccount).
It’s always good to write about security in general. Creating awareness and informing users to improve their security is always a good idea and we’d love to read the article once it’s published. But we’d be very sad if one could read your post in a way that would imply that Yoast SEO is making it easier for hackers.
Could you share your post with us once it’s live?
Thanks and regards,
Ben Vaassen
Lead Support Engineer at Yoast
Big Thank You: To my friend and colleague Bill Hartzer who allowed me to install a fresh version of Yoast on one of his websites to determine the default settings. Bill does quite a bit of blogging on SEO and Domain topics over on his website and is fairly active on Twitter.
